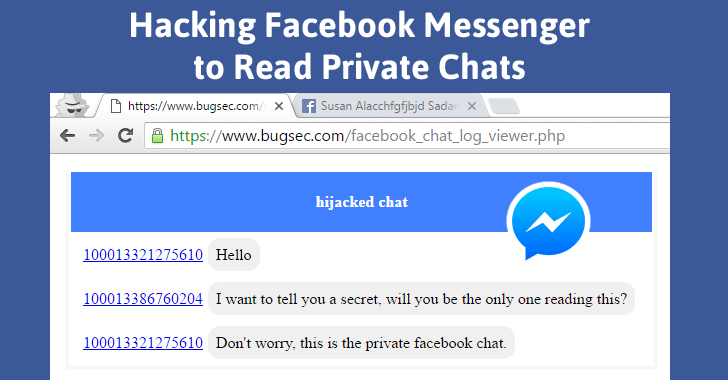
A security researcher has found a critical Vulnerability in the Facebook Messenger that can allow attackers to read all secret conversation, affecting the privacy of around 1 billion Facebook messenger users.
Ysrael Gurt, the security researcher at BugSec and Cynet, reported a cross-origin bypass attack against Facebook Messenger that allows hackers to access your chat, photos and attachments as well.
To exploit this vulnerability, an attacker found a simple trick, victim just need to visit the malicious website, that’s it.
Once a victim visited the website, all the victim’s secret conversation would be accessible to the hacker, whether the victim is using Facebook’s mobile app or web browser. Because these flaws affected both the web chat as well mobile application.
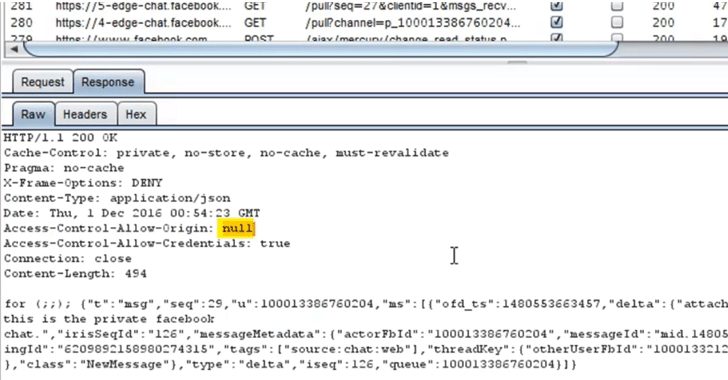
Dubbed “Originull” in fact, the vulnerability is in the Facebook chats are managed from a server located at {number}-edge-chat.facebook.com, which is different from actual Facebook domain (www.facebook.com).
“Communication between the JavaScript and the server is done by XML HTTP Request (XHR). In order to access the data that arrives from 5-edge-chat.facebook.com in JavaScript, Facebook must add the “Access-Control-Allow-Origin” header with the caller’s origin, and the “Access-Control-Allow-Credentials” header with “true” value, so that the data is accessible even when the cookies are sent,” Gurt explained.
The main issue was misconfigured cross-origin header implementation on Facebook’s chat server domain, which is allowing the attackers to bypass the origin checks and access the Facebook chats from a malicious website.
However, the Facebook Messenger’s Secret Conversation is not affected by this vulnerability, But, the Secret Conversation is only available for mobile app.
“This security flaw meant that the messages of 1-billion active monthly Messenger users were vulnerable to attackers,” said Stas Volfus, Chief Technology Officer of BugSec.
“This was an extremely serious issue, not only due to the high number of affected users, but also because even if the victim sent their messages using another computer or mobile, they were still completely vulnerable.”
Watch the Facebook originull video:
You can read the full blog post on Cynet.